The endpoints that are often targeted by ransomware attacks are local drives, although this may be changing. Although cloud storage has traditionally been seen as a secure storage device against ransomware assaults, new study from Proofpoint raises concern.
A feature in the Microsoft 365 software that could be abused to encrypt files kept on OneDrive and SharePoint has been found by Proofpoint researchers. In reality, if the ransomware attack is severe enough, you won’t be able to restore your files without special backups or decryption keys obtained directly from the perpetrators. Let’s investigate this ransomware attack on OneDrive and SharePoint files in more detail. Let’s first take a quick look at ransomware, though.
Quick Overview of Ransomware
One form of malware called ransomware commandeers the victim’s account or system to obstruct access and encrypt data. Attackers using ransomware have a variety of techniques to gain access to the victim’s system. The most common method is phishing, in which the user is duped into sharing login information or clicking a malicious link or file that infects the machine with malware. Alternately, system flaws may be used to access the user’s system or account.
Once ransomware attackers have gained access to the system, they can perform a variety of tasks, such as block access, encrypt data, mine bitcoins, and more. The majority of the time, the data is encrypted by the attackers, who then demand a ransom to unlock it. Additionally, many attackers even give discounts for early payments to encourage the victim to pay the ransom immediately and without hesitation. The attackers also give the victim a thorough, step-by-step tutorial on how to finish the transaction.
Your files in OneDrive and SharePoint can now be locked thanks to a new vector.
The OneDrive and SharePoint data in the accounts of infected users can be encrypted by ransomware attackers thanks to a risky feature in Microsoft 365, according to Proofpoint. The files could then only be accessible again by purchasing the decryption key or retrieving the prior dedicated backup.
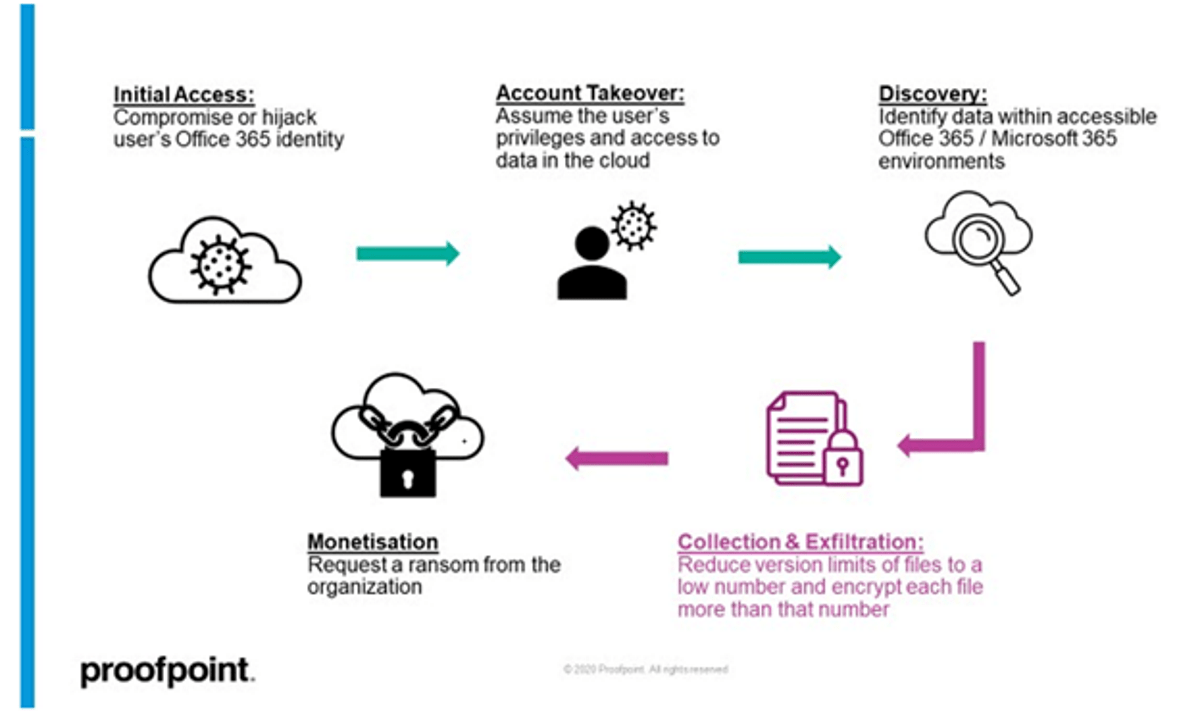
The research by Proofpoint indicates the “AutoSave” feature of Microsoft 365 as a potential threat. This feature is meant to make copies of older versions of files stored on OneDrive/SharePoint. The attack chain as pointed out by Proofpoint could go as follows:
Initial Access:
Attackers begin by initially acquiring access to the OneDrive or SharePoint account(s) of the user(s) by stolen login information, convincing the victim to grant third-party OAuth apps, or taking over a logged-in user’s web session.
Account Takeover:
Once an attacker has gained access to a user’s account, they can view all of the files that person has saved in OneDrive or SharePoint.
Collection and Exfiltration:
Set the file’s version limit to a low value, such as “1,” and then encrypt the file more than the version limit allows, for example, twice if the version limit is set to 1. Attackers can also use the encrypted files to exfiltrate information, which is a second kind of extortion.
The attackers can then demand a ransom to unlock the data if the original versions of the files are lost but the encrypted versions are still present in the user account.
PowerShell scripts, command line interface scripts, and Microsoft APIs can all be used to automate the aforementioned tasks.
One property that determines how many saved versions a user can edit is used to build the document library in OneDrive and SharePoint. When a user lowers the document library version limit, it signifies that new changes to the file will make reverting to earlier versions very challenging.
Attackers can therefore either construct a large number of file versions or modify the version limit to simply “1” and then encrypt each file more than the allowed number of times. For instance, the typical OneDrive account has a 500 version limit. As a result, hackers have 501 chances to modify document library files. Every file’s initial version is thus the 501st version file, which is no longer available. As an alternative, they may encrypt the file twice and set the version limit to 1.
What Should You Do if Someone Hacks You and Demands a Ransom?
There are definite indications that ransomware attacks can happen in your cloud storage based on the aforementioned Proofpoint research and the weak “AutoSave” feature of Microsoft 365. When Proofpoint brought up this issue with Microsoft, the latter responded that older versions of the files could be restored for an additional 14 days with the assistance of Microsoft Support. Proofpoint did adhere to that, but it was unable to restore earlier versions.
Therefore, the only quick solution if you become a victim of a ransomware attack and your data is encrypted on your cloud account or local disk is to pay the ransom and obtain the decryption key. However, this method is not advised because you can never be sure that the decryption key will work, that you will recover the data, or that the attacker won’t demand more money. Additionally, it incites perpetrators to carry out additional similar attacks.
Following the ransomware assault, you should take the following actions, which are advised:
- Isolate and disconnect the compromised device.
- Speak to the local authorities.
- To attempt to eliminate malware, get in touch with a cybersecurity specialist.
- Look for any data backups you may have already made, or if you shared it with others, try to restore the data from their system.
In conclusion, you must take all reasonable steps to restore the data without paying the ransom.
How to Securely Store Files (on Your PC)
Today, there is a real danger from ransomware and other intrusions. By 2025, cybercrimes will cost the global economy $10.5 trillion annually, according to Cybersecurity Ventures. Therefore, it is crucial now more than ever to save our data and files safely. The following are some practical methods for safely storing files on your computer:
- Windows encryption for files and folders. Right-click the file or folder, select Properties, then select Advanced, choose Encrypt contents to encrypt data, and finally select OK.
- Access to your files and folders in Windows can be restricted. Right-click the file or folder and select Properties > Security > Edit to accomplish that. Select the user or group after that, and then click “Deny Access.” By doing this, the user or group will then need to input an administrative password in order to access that file or folder.
- Encrypt important files and directories using software from other parties.
- Create regular backups of your files on an external hard drive or in the cloud.
- Put antivirus software to use.
- Keep your applications and operating system patched and up to date.
- Don’t grant all software administrator access.
In conclusion, you should take all precaution you can to secure the contents on your PC. While these precautions cannot completely ensure security from intrusions, they can significantly reduce the likelihood.
